Introduction
SELinux (Security-Enhanced Linux) is a Mandatory Access Control (MAC) system built into the Linux kernel.
One of the key features of SELinux is that it allows sysadmins to block unauthorized access to system resources. This security architecture enforces the separation of privilege between system users and processes, enabling administrators to manage access to resources more efficiently.
In this text, learn what Security-Enhanced Linux (SELinux) is, how it works, and how to configure it properly.

What Is SELinux?
Security-Enhanced Linux (SELinux) is a security architecture created by the United States National Security Agency (NSA) and Red Hat. This security module is available for most Linux distributions but is mainly used on RHEL and Fedora.
SELinux enforces Mandatory Access Control (MAC) policies. MAC is a type of security system that allows sysadmins to set a centralized security access policy and specify which users and processes have access to specific resources. The system also operates on a least-privilege model, blocking access to the resources by default.
With SELinux, sysadmins differentiate a user from the applications the user runs. For example, the user shell has complete access to the home directory. However, if the user runs a mail client, SELinux blocks the client from accessing specific home directory parts.
SELinux also increases the level of protection by separating security policies and enforcement of security decisions inside the kernel. The separation gives sysadmins greater control over the overall system security. Additional protection also stems from SELinux being integrated into the Linux kernel, which means it is always running, and users and processes cannot disable it.
How Security-Enhanced Linux Works?
SELinux works by implementing mandatory access controls (MAC). With MAC, sysadmins define which users and processes have access to specific resources rather than relying on less secure broadly-defined permissions. To accomplish this, SELinux uses security policies.
SELinux Policies
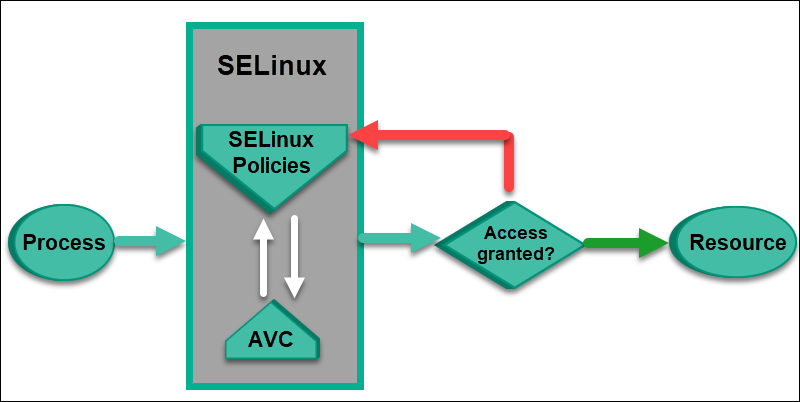
SELinux blocks all applications and users by default, allowing access only to those specified in the security policies.
Security policies are a set of rules that instruct SELinux who has access to which system resource. These rules establish the permissions for each user, process, and resource.
SELinux cashes every decision (block or allow access) in the Access Vector Cache (AVC), which speeds up the access control process.
When a process requests access to a resource, SELinux consults AVC to check whether a decision has already been made for that request. If yes, it rejects the request immediately, saving time and resources. If not, SELinux consults the policy rules and makes the decision.
One critical feature of Security-Enhanced Linux is the ability to specify different permissions for different processes. For example, an admin sets a policy that allows a web server process to read and write to the document root but blocks other processes.
SELinux also supports context-based access controls. For example, a sysadmin sets a policy allowing a web server to read and write to the root only under certain conditions, i.e., when the request comes from a trusted IP address.
SELinux Labels and Type Enforcement
Type enforcement and labeling are essential concepts for SELinux.
SELinux uses labels with access control policies to determine which actions to allow for each resource. Admins assign labels to every process, network, port, or file. The labels consist of the following:
- User. The Linux user that is being mapped to a SELinux user.
- Role. The user's authorized role. Each role is authorized for a specific type.
- Type. Determines the type enforcement. Each type enforces a set of permissions.
- Level (optional). The security clearance level, expressed as a range.
The labels are part of security policies, which specify the kinds of access allowed for each label type.
Label syntax is:
user:role:type:levelLabel type is the most critical concept for targeted policy. The process of checking the label type of the security policies is type enforcement. Type enforcement ensures that only authorized processes and users have access to particular resources.
Each type is associated with a set of permissions that define actions permitted for that type. When a process or user attempts to access a resource, SELinux compares the resource type to the process or user type. Next, the module grants or denies access based on the permissions associated with those types.
SELinux Modes
One key feature of SELinux is the ability to operate in different modes, which allows sysadmins to fine-tune system security.
There are three main SELinux modes:
- Enforcing mode. The default and most secure SELinux mode. In this mode, SELinux enforces the access control policies set by the sysadmin and does not allow users to override them. If a user or process attempts to access a resource not authorized by the policies, SELinux denies the request and logs the decision in AVC.
- Permissive mode. Less secure than enforcing mode but still provides protection. In this mode, SELinux does not enforce the policies but logs events when a user or process attempts to access a resource blocked off by the policies. This enables sysadmins to monitor the system for potential security issues and make any necessary policy changes before authorizing the enforcing mode.
- Disabled mode. The least secure mode as it does not protect system resources. In this mode, SELinux does not enforce access control policies. This mode is useful for testing or debugging.
How to Configure SELinux?
Linux comes with preinstalled SELinux security policies, which simplifies the configuration. In addition, the architecture also allows administrators to define the security policies themselves.
There are several ways to configure SELinux, either permanently or during the current session.
Note: A user account with root or sudo privileges is necessary to configure SELinux.
Configure SELinux Permanently
To set up an SELinux configuration that won't reset after the reboot, edit the /etc/selinux/config file. This file contains SELinux configuration options, including the mode in which SELinux should operate.
To set the mode to enforcing, permissive, or disabled, change the SELINUX variable accordingly. For instance, to set SELinux to permissive mode, follow these steps:
1. Open the SELinux config file in a text editor of your choice. This tutorial uses Vim.
sudo vim /etc/selinux/config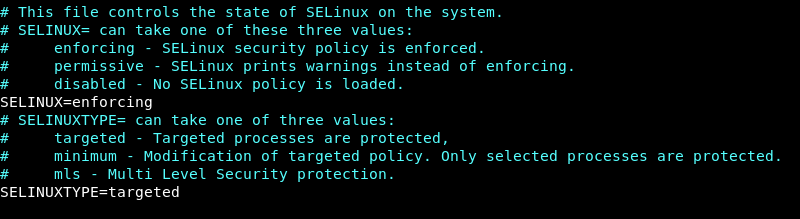
2. Set the SELINUX variable to permissive with:
SELINUX=permissive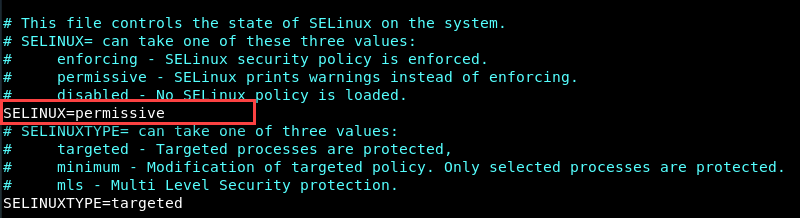
4. Reboot the system.
5. Verify the change with:
sudo sestatus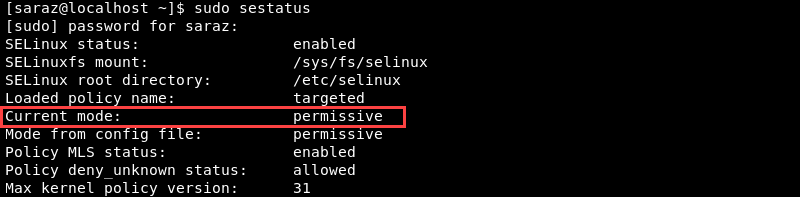
The sestatus command shows that the current mode of SELinux is permissive and verifies the change in the config file.
Configure SELinux Temporarily
SELinux also provides commands for setting up the configuration for the current session only. Once the session restarts, the settings reset to those in the configuration file.
The setenforce command turns enforcing mode on (with variable 1) or off (with variable 0). To activate enforcing mode, run:
sudo setenforce 1The command provides no output. Verify the result using either sestatus or getenforce.
To check whether SELinux is in enforcing mode with sestatus, run:
sudo sestatus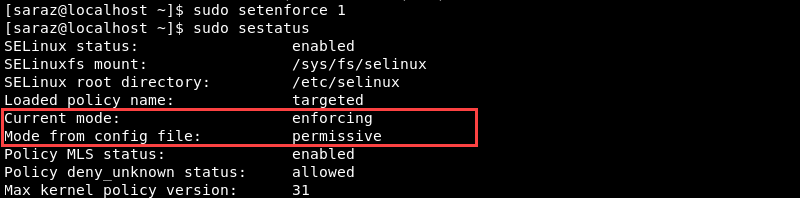
The output shows that the current mode is enforcing, while the configuration file variable is still permissive. Restarting the terminal reverts the current mode to permissive.
Another way to check the current mode is with the getenforce command:
sudo getenforce
Linux vs. SELinux: What are the Differences?
SELinux and Linux are two distinct entities. Linux is an operating system, and SELinux is a security module that is a part of the Linux kernel.
Differences between the standard Linux setup and SELinux are:
- The purpose. As an operating system, Linux manages the hardware and software resources, providing the foundation for software development. On the other hand, SELinux is a security component that protects Linux from malicious software and unauthorized access.
- Access control enforcement. In standard Linux setups, users and apps have unlimited access to the system as long as they have the necessary privileges. The mechanism is Discretionary Access Control (DAC). However, SELinux works differently. Security-Enhanced Linux allows administrators to specify permissions for each user, process, and resource on the system. SELinux blocks any unauthorized access attempts, while sysadmins use security policies to determine when a user has access to specific operating system processes or files.
App Armor vs. SELinux: What are the Differences?
AppArmor is SELinux's main competitor. While both MAC security frameworks protect systems from malicious software and unauthorized access to system resources, AppArmor and SELinux differ in many aspects:
- Unlike SELinux, AppArmor does not use type enforcement but manages access using configuration files. AppArmor uses profiles, a set of rules for allowing or blocking each program. These profiles exist for each program and are a part of a configuration file. When a program attempts to perform an action not allowed by the profile, AppArmor blocks the action and logs the event. SELinux uses MAC, enabling sysadmins to specify permissions for each user, process, and resource on the system.
- AppArmor is mainly used on SUSE and Ubuntu, even though both systems are available for any Linux distribution.
- AppArmor is easier to learn, configure, and manage. However, the system does have a slower startup time, less flexibility, and a lower control level. SELinux is more complex to configure and manage, as it gives control to sysadmins and allows for fine-grained control based on users, processes, and contexts.
Conclusion
After reading this article, you know what Security Enhanced Linux (SELinux) is and how to configure a simple security configuration. Next, learn how to enable SELinux in CentOS.